*Based on the list of 2025 Fortune 500® companies with recurring revenue to Qlik during the 12-month period ending June, 2025. Fortune 500 is a registered trademark of Fortune Media IP Limited. Qlik is not affiliated with or endorsed by Fortune.
Do Data Differently
We deliver AI-powered analytics and robust data integration solutions tailored to meet the evolving needs of enterprise organizations.
Try for FreeSeamless data integration and powerful Al-driven analytics to drive better business decisions
Accelerate Your AI Transformation With Qlik
Qlik combines trusted data with built-in AI to deliver smarter, faster, and more responsive insights, custom predictive models, and intelligent experiences for front or back of office.
Unified platform for data, analytics, and AI
Built-in generative and predictive intelligence
Trusted governance for explainable results
75% of the Fortune 500® use Qlik*
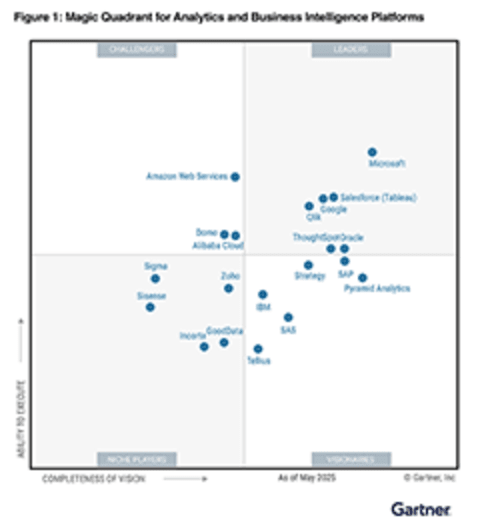
Team up with a Gartner® Magic Quadrant™ leader
in three categories
Powering the Future of AI
Join Qlik’s Market Intelligence Lead, Dan Sommer, for a sharp look at what’s ahead. In Powering the Future of AI: Dare to Orchestrate Data, Agents, and Roles, you’ll see why bouncing between control and innovation stalls progress – and get a clear framework to move forward.